Free Download Akamai Technologies Infection Monkey for Windows PC. It is an open-source breach and attack simulation (BAS) platform designed to assess the security posture of your network infrastructure. It allows you to simulate various attack scenarios to identify vulnerabilities and gaps in your defenses. It is a powerful tool to help organizations proactively strengthen their security measures and prevent potential cyber threats.
Overview of Infection Monkey
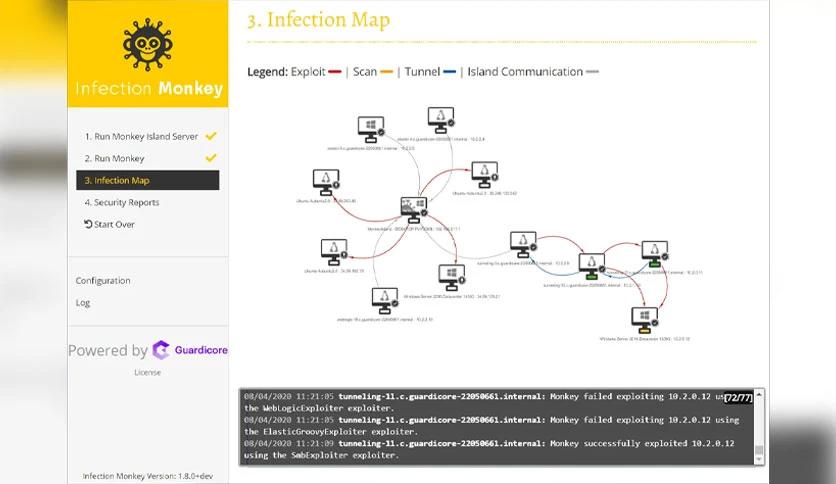
It operates by deploying a virtual monkey within your network environment, which simulates the behavior of an actual attacker. This monkey then attempts to propagate across the network by exploiting vulnerabilities and misconfigurations in systems and services. Doing so helps organizations understand how an actual cyber attacker might move laterally within their infrastructure and compromise sensitive data.
Simulating Attack Scenarios
One of the key features is its ability to simulate a wide range of attack scenarios. From phishing attacks to brute-force attempts, the platform can mimic various tactics used by cybercriminals. By running these simulations, organizations can identify weak points in their defenses and proactively address them before real attackers exploit them.
Assessing Security Controls
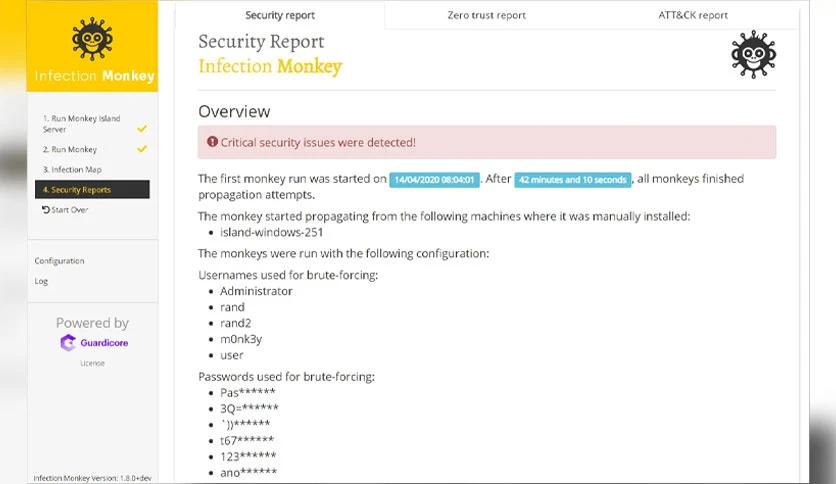
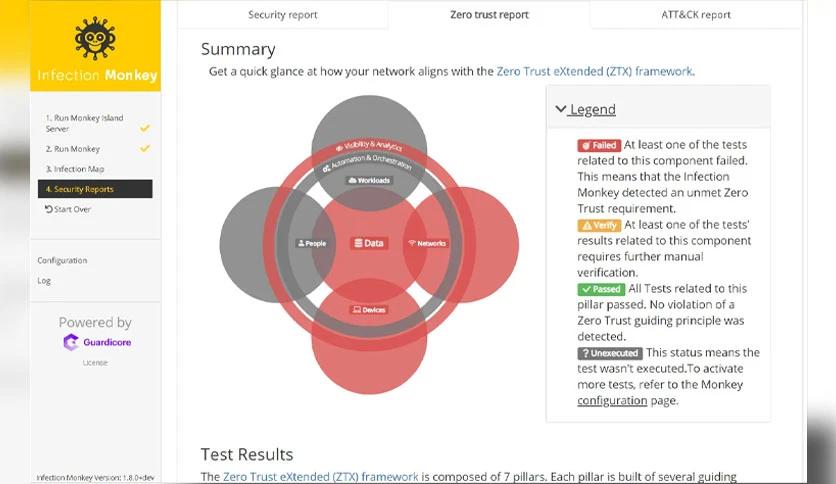
It also helps evaluate the effectiveness of existing security controls. It tests the resilience of firewalls, intrusion detection systems (IDS), and other security measures by attempting to bypass them during simulated attacks. This allows organizations to identify weaknesses in their security infrastructure and fine-tune their defenses accordingly.
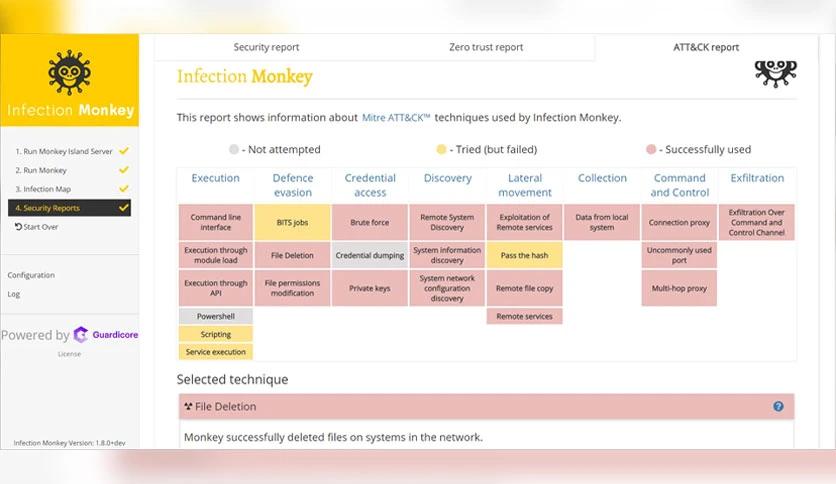
Real-Time Reporting and Analysis
Another advantage of using it is its comprehensive reporting and analysis capabilities. The platform provides real-time feedback on the success of its attack simulations, including details on which systems were compromised and how the attack propagated. This information is invaluable for security teams, enabling them to prioritize remediation efforts and allocate resources more effectively.
System Requirements
- Operating System: Windows 11/10/8.1/8/7
- Processor: Minimum 1 GHz Processor (2.4 GHz recommended)
- RAM: 2GB (4GB or more recommended)
- Free Hard Disk Space: 200MB or more is recommended
Conclusion
Infection Monkey is an invaluable tool for organizations looking to enhance their cybersecurity defenses. Simulating realistic attack scenarios and assessing the effectiveness of existing security controls enables businesses to identify and address vulnerabilities before malicious actors can exploit them. Its user-friendly interface and powerful features make it a must-have for any organization serious about safeguarding its digital assets.
Leave a comment
Your email address will not be published. Required fields are marked *